If a file is copied from one NTFS partition to another, even over a network, the virus and host will be transmitted. If the virus is executed on a non-NTFS partition or if the host in the secondary stream is missing, the virus will display a message revealing itself in a message box. When on the Internet, the virus will attempt to connect to the virus writer’s website in Japan and update the virus. The virus writer has created at least four other virus modules that the original virus downloads and executes. Using this method, the virus writer could continually update and add functionality to the virus. The AUTOEXEC.BAT file is modified and the following text added, “Win95/Babylonia by Vecna 1999”.
A Trojan Horse Virus is a type of malware that downloads onto a computer disguised as a legitimate program. The delivery method typically sees an attacker use social engineering to hide malicious code within legitimate software to try and gain users’ system access with their software. The URL contains the path “~tilde/pub/cia-bin/etc”.
VIRUSES AND OTHER MALICIOUS CODE
Select type of files you want to restore and click Next. Various dubious web-sources can contain malicious scripts or hyperlinks that can infect your system. Our advice – avoid visiting P2P sites and websites with illegal content . Use only legitimate services and remember – there’s no free lunch in this world. While 7-Zip may sound like a good name for a PC virus, it’s actually a legitimate utility that compresses and decompresses files. It also comes with a built-in file manager that helps you manage those files.
- The plugins for each category will instantly show.
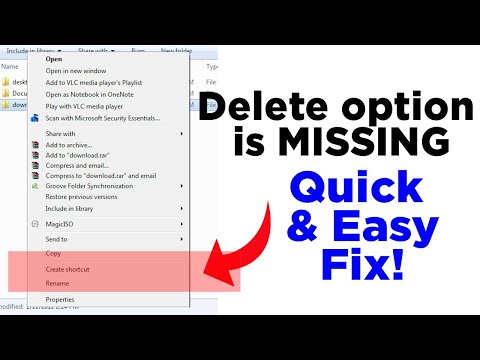
- And after choosing the language, time and input method, enter the following interface and click Repair your computer to run a startup.
- Problems with opening the file may arise due to various reasons.
S0263 TYPEFRAME A Word document delivering TYPEFRAME prompts the user to enable macro execution. S0266 TrickBot TrickBot has attempted to get users to launch malicious documents to deliver its payload. S0665 ThreatNeedle ThreatNeedle relies on a victim to click on a malicious document for initial execution. S1037 STARWHALE STARWHALE has relied on victims opening a malicious Excel file for execution. S0390 SQLRat SQLRat relies on users clicking on an embedded image to execute the scripts. S0433 Rifdoor Rifdoor has been executed from malicious Excel or Word documents containing macros.
How To Open a DLL File – Introduction
It is not a good system, but better than nothing. The freeimage.dll file can be recompiled based on custom changes , and so there can be many variations of this DLL file floating around. Your anti-virus program may be noting that your file doesn’t match the common “freeimage.dll” that’s available, and might assume it’s a sneaky replacement.
S0585 Kerrdown Kerrdown has gained execution through victims opening malicious files. S0531 Grandoreiro Grandoreiro has infected victims via malicious attachments. G0061 FIN8 FIN8 has used malicious e-mail attachments download here to lure victims into executing malware.